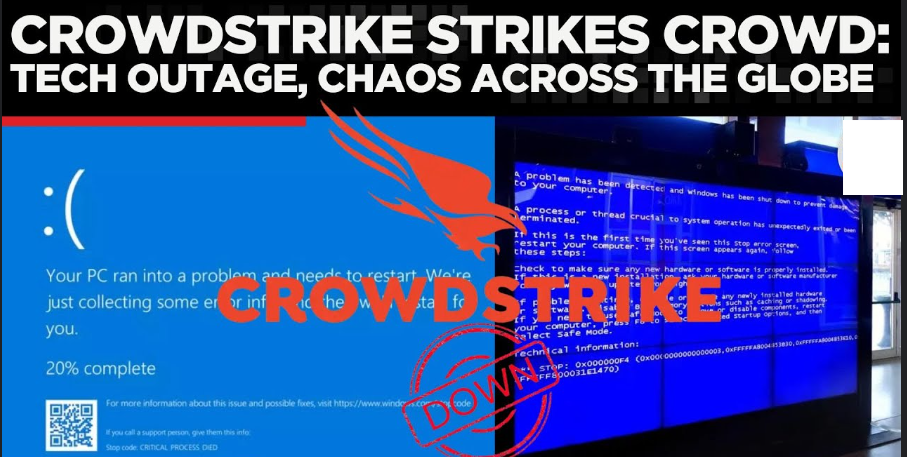
Crowdstrike Windows outage 2024 and how to quickly fix it
Overview of CrowdStrike’s Products and Services CrowdStrike is a leading name in the cybersecurity industry, renowned for its comprehensive and advanced security solutions. Here’s a detailed overview of CrowdStrike’s products and services: Endpoint and Cloud Workload Protection CrowdStrike Falcon is the flagship product, offering robust protection for endpoints and cloud workloads. Using artificial intelligence and […]
Crowdstrike Windows outage 2024 and how to quickly fix it Read More »